https://www.bankchb.com/csr/mashup_eng.jsp?funcId=9fff75e315
PGh0bWw+IDxoZWFkPjxcL2hlYWQ+IDxib2R5PiAgPGdhcmRlbj4gICA8ZnVuY3M+ICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJhcmVhX2Z1bGxcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU5OTk2XHU5ODAxXCIgZGVzY3JpcHRpb249XCJcdTk5OTZcdTk4MDFcIiBpZD1cImluZGV4XCIgcGFnZT1cImluZGV4XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgPGZ1bmMgbGF5b3V0PVwic3ViYXJlYVwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTg0NjNcdTRFOEJcdTk1NzdcdTc2ODRcdThBNzFcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiMDkyY2MyYzAxNVwiIHBhZ2U9XCIwOTJjYzJjMDE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICA8ZnVuYyBsYXlvdXQ9XCJcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU2QzM4XHU3RThDXHU3NjdDXHU1QzU1XHU5MDRCXHU0RjVDXHU2QTVGXHU1MjM2XCIgZGVzY3JpcHRpb249XCJcdTZDMzhcdTdFOENcdTc2N0NcdTVDNTVcdTkwNEJcdTRGNUNcdTZBNUZcdTUyMzZcIiBpZD1cIjIzNThiNTMyMTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU2QzM4XHU3RThDXHU3NjdDXHU1QzU1XHU3RDQ0XHU3RTU0XHU2N0I2XHU2OUNCXHU1M0NBXHU5MDRCXHU0RjVDXHU2QTVGXHU1MjM2XCIgZGVzY3JpcHRpb249XCJcdTZDMzhcdTdFOENcdTc2N0NcdTVDNTVcdTdENDRcdTdFNTRcdTY3QjZcdTY5Q0JcIiBpZD1cIjBiZjEwM2QwMTVcIiBwYWdlPVwiMGJmMTAzZDAxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU1MjI5XHU1QkIzXHU5NURDXHU0RkMyXHU0RUJBXHU1QzA4XHU1MzQwXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjVlNGI3MjA5MTVcIiBwYWdlPVwiNWU0YjcyMDkxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU5MUNEXHU1OTI3XHU0RTNCXHU5ODRDXHU5NDUxXHU1MjI1XHU4MjA3XHU3QkExXHU3NDA2XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cImY1NzljYjI4MTVcIiBwYWdlPVwiZjU3OWNiMjgxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmFyZWFcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU2QzM4XHU3RThDXC9cdTRGMDFcdTY5NkRcdTc5M0VcdTY3MDNcdThDQUNcdTRFRkJcdTU4MzFcdTU0NEFcdTY2RjhcIiBkZXNjcmlwdGlvbj1cIkNTUlx1NTgzMVx1NTQ0QVx1NjZGOFwiIGlkPVwiN2M1MDA5MTExNVwiIHBhZ2U9XCI3YzUwMDkxMTE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cImh0dHBzOlwvXC93d3cuYmFua2NoYi5jb21cL2NzclwvbWFzaHVwLmpzcD9mdW5jSWQ9NjZjNGM1MTExNVwiPjxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NTIyOVx1NUJCM1x1OTVEQ1x1NEZDMlx1NEVCQVx1NTU0Rlx1NTM3N1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCIwNTQxZWE1NjE1XCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJodHRwczpcL1wvd3d3LmJhbmtjaGIuY29tXC9mcm9udGVuZFwvc3Rha2Vob2xkZXJRdWVzdGlvbi5qc3BcIj48XC9mdW5jPiAgICAgPFwvZnVuYz4gICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTZDMzhcdTdFOENcdTk3Q0NcdTYwMjdcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYmJiN2JhNTIxNVwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+ICAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NEYwMVx1Njk2RFx1Njk4Mlx1NkNDMVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI5ZTEyYWE1ZDE1XCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTRGMDFcdTY5NkRcdTY5ODJcdTZDQzFcdTgyMDdcdTcxREZcdTkwNEJcdTdFM0VcdTY1NDhcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiM2M3YmM4N2QxNVwiIHBhZ2U9XCIzYzdiYzg3ZDE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU3QTA1XHU1MkQ5XHU2Q0JCXHU3NDA2XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjk4M2EwZjQ1MTVcIiBwYWdlPVwiOTgzYTBmNDUxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NTE2Q1x1NTNGOFx1NkNCQlx1NzQwNlwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJlZWU5NDkzYjE1XCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTUxNkNcdTUzRjhcdTZDQkJcdTc0MDZcdTY3QjZcdTY5Q0JcdTgyMDdcdTg0NjNcdTRFOEJcdTY3MDNcdTkwNEJcdTRGNUNcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiMjM1NWQ1MGExNVwiIHBhZ2U9XCIyMzU1ZDUwYTE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU4NDYzXHU0RThCXHU2NzAzXHU3RTNFXHU2NTQ4XHU4MjA3XHU4NUFBXHU5MTZDXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cImE1YzdlYmU3MTVcIiBwYWdlPVwiYTVjN2ViZTcxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdThBQTBcdTRGRTFcdTdEOTNcdTcxREZcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiMjAzYmQ1ZWIxNVwiIHBhZ2U9XCIyMDNiZDVlYjE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTZDRDVcdTRFRTRcdTkwNzVcdTVGQUFcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiZWY5MDEwMTQxNlwiIHBhZ2U9XCJlZjkwMTAxNDE2XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTZEMTdcdTkzMjJcdTk2MzJcdTUyMzZcdTgyMDdcdTYyNTNcdTY0Q0FcdThDQzdcdTYwNTBcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYTNiYWIzZTMxNlwiIHBhZ2U9XCJhM2JhYjNlMzE2XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTk4QThcdTk2QUFcdTdCQTFcdTc0MDZcdTgyMDdcdTdBM0RcdTY4MzhcdTUyMzZcdTVFQTZcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYzBjNDU2MGExNVwiIHBhZ2U9XCJjMGM0NTYwYTE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1OThBOFx1OTZBQVx1N0JBMVx1NzQwNlx1ODIwN1x1N0EzRFx1NjgzOFx1NTIzNlx1NUVBNlwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJlYjMwNzExNTE2XCIgcGFnZT1cImViMzA3MTE1MTZcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTY1QjBcdTgyMDhcdTk4QThcdTk2QUFcdTdCQTFcdTc0MDZcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYWE0ZDNiNDMxNlwiIHBhZ2U9XCJhYTRkM2I0MzE2XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU2NjdBXHU2MTY3XHU4Q0ExXHU3NTIyXHU2QjBBXHU3QkExXHU3NDA2XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjRmODQ1OGIzMTZcIiBwYWdlPVwiNGY4NDU4YjMxNlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1OENDN1x1OEEwQVx1NUI4OVx1NTE2OFx1MzAwMVx1NTAwQlx1OENDN1x1OTYzMlx1OEI3N1x1ODIwN1x1NzFERlx1Njk2RFx1NzlEOFx1NUJDNlx1NEZERFx1OEI3N1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI1ZmE3MmFjZTE1XCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdThDQzdcdThBMEFcdTVCODlcdTUxNjhcdTZBNUZcdTUyMzZcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiNGRhMDEzZWExNVwiIHBhZ2U9XCI0ZGEwMTNlYTE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU1MDBCXHU0RUJBXHU4Q0M3XHU2NTk5XHU0RkREXHU4Qjc3XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjMyNmQxNmM4MTVcIiBwYWdlPVwiMzI2ZDE2YzgxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NzFERlx1Njk2RFx1NzlEOFx1NUJDNlx1NEZERFx1OEI3N1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJhNTRkNDAwMTE1XCIgcGFnZT1cImE1NGQ0MDAxMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8XC9mdW5jPiAgICAgPFwvZnVuYz4gICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTZDMzhcdTdFOENcdTkxRDFcdTg3OEQgXHU2QzM4XHU3RThDXHU3NEIwXHU1ODgzXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cImY4NTA4MjM4MTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU1MTZDXHU1RTczXHU1Rjg1XHU1QkEyXHU4MjA3XHU5NjMyXHU4QTUwXHU1Qjg5XHU1MTY4XHU3REIyXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjgwOTkzZDMzMTVcIiBwYWdlPVwiODA5OTNkMzMxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU2NTc4XHU0RjREXHU1Mjc1XHU2NUIwXHU2NzBEXHU1MkQ5XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjQxZTFiZTFkMTVcIiBwYWdlPVwiNDFlMWJlMWQxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU2NjZFXHU2MEUwXHU5MUQxXHU4NzhEXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cImFmZmUyMDQ0MTZcIiBwYWdlPVwiYWZmZTIwNDQxNlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU4Q0FDXHU0RUZCXHU5MUQxXHU4NzhEXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjEyNzRhNjdmMTVcIiBwYWdlPVwiMTI3NGE2N2YxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTdEQTBcdTgyNzJcdThGNDlcdTU3OEJcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiZDMxMTFmNjQxNVwiIHBhZ2U9XCJkMzExMWY2NDE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU4Q0FDXHU0RUZCXHU2Mjk1XHU4Q0M3XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjg0NjMxOWZkMTVcIiBwYWdlPVwiODQ2MzE5ZmQxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NzZFMVx1ODA3N1x1NjM4OFx1NEZFMVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCIxOTg0YWQ3YTE1XCIgcGFnZT1cIjE5ODRhZDdhMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdThENjRcdTkwNTNcdTUzOUZcdTUyNDdcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiOGJjNDQyNTIxNVwiIHBhZ2U9XCI4YmM0NDI1MjE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgPFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NkMyM1x1NTAxOVx1NjZBOFx1ODFFQVx1NzEzNlx1NzZGOFx1OTVEQ1x1NjNFRFx1OTczMlwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI5NTZmMGQzZDE1XCIgcGFnZT1cIjk1NmYwZDNkMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NUMwRVx1NTE2NVx1NzRCMFx1NTg4M1x1NkMzOFx1N0U4Q1x1NkExOVx1NkU5NlwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI0OGU3YTVmMzE1XCIgcGFnZT1cIjQ4ZTdhNWYzMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NkVBQlx1NUJBNFx1NkMyM1x1OUFENFx1NkUxQlx1OTFDRlx1NTNDQVx1N0JBMVx1NzQwNlwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJjYTg3ZmIxMTE1XCIgcGFnZT1cImNhODdmYjExMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NEY0RVx1NzhCM1x1NzkzQVx1N0JDNFx1NTgzNFx1NTdERlx1NUVGQVx1N0Y2RVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJkMTZjZDlkMTE1XCIgcGFnZT1cImQxNmNkOWQxMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1OTdGRlx1NjFDOVx1NEUyNlx1NjNBOFx1NTJENVx1N0RBMFx1ODI3Mlx1OEZBNlx1NTE2Q1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJjMGM3MjU5ZjE1XCIgcGFnZT1cImMwYzcyNTlmMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NEY5Qlx1NjFDOVx1NTU0Nlx1N0JBMVx1NzQwNlwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJhN2I5NDMwYzE1XCIgcGFnZT1cImE3Yjk0MzBjMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NkMzOFx1N0U4Q1x1OENDN1x1OEEwQVx1NUMwOFx1NTM0MFwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCIzOGE2N2FhZTE1XCIgcGFnZT1cIjM4YTY3YWFlMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgIDxcL2Z1bmM+ICAgICA8ZnVuYyBsYXlvdXQ9XCJcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU1RTc4XHU3OThGXHU4MDc3XHU1ODM0IFx1NzkzRVx1NjcwM1x1NTE3MVx1ODc4RFwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI2OTAzOTQwMTE1XCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NEVCQVx1NkIwQVx1NEZERFx1OTY5Q1x1ODIwN1x1NTkxQVx1NTE0M1x1NUU3M1x1N0I0OVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI4NWQ2ODNhMDE1XCIgcGFnZT1cIjg1ZDY4M2EwMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NEVCQVx1NjI0RFx1NTQzOFx1NUYxNVx1ODIwN1x1NzU1OVx1NEVGQlwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCIwNjY5ZDNiZTE1XCIgcGFnZT1cIjA2NjlkM2JlMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NTRFMVx1NURFNVx1NTdGOVx1NTI5Qlx1NzY3Q1x1NUM1NVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJhZTE2NDVlYTE1XCIgcGFnZT1cImFlMTY0NWVhMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1ODA3N1x1Njk2RFx1NUI4OVx1NTE2OFx1ODIwN1x1NTA2NVx1NUVCN1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJkM2FhOWJkYzE1XCIgcGFnZT1cImQzYWE5YmRjMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NTE2Q1x1NzZDQVx1N0I1Nlx1NzU2NVx1ODIwN1x1NUY3MVx1OTdGRlx1NTI5QlwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJlZThlODI4ZDE1XCIgcGFnZT1cImVlOGU4MjhkMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1OTc1RVx1OENBMVx1NTJEOVx1OTFEMVx1ODc4RFx1NjUyRlx1NjMwMVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI4NjFjMzAzZjE1XCIgcGFnZT1cIjg2MWMzMDNmMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgIDxcL2Z1bmM+ICAgICA8ZnVuYyBsYXlvdXQ9XCJcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU2OUFFXHU4MDAwXHU4MjA3XHU4MEFGXHU1QjlBXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cImVmNzdmYTkyMTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU0RjAxXHU2OTZEXHU2QzM4XHU3RThDXHU3RTNFXHU2NTQ4XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjg0NWI3ZmJjMTVcIiBwYWdlPVwiODQ1YjdmYmMxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU1NzBCXHU5NjlCXHU4QThEXHU4QjQ5XHU2QTE5XHU3QUUwXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjUxMjU0MGNmMTVcIiBwYWdlPVwiNTEyNTQwY2YxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgPFwvZnVuYz4gICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTUzQ0JcdTU1ODRcdTkwMjNcdTdENTBcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYTA1OTRlNWIxNVwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTUzQ0JcdTU1ODRcdTkwMjNcdTdENTBcdTVFNzNcdTUzRjBcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYmMwNWNjM2IxNVwiIHBhZ2U9XCJiYzA1Y2MzYjE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICA8XC9mdW5jPiAgICA8XC9mdW5jPiAgICA8ZnVuYyBsYXlvdXQ9XCJcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiXHU1MjZGXHU5MDc4XHU1NUFFXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cInRvcG1lbnUxXCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJFTkdMSVNIXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjUzNmZiYTg2MTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cImluZGV4X2VuZy5qc3BcIj48XC9mdW5jPiAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NUI5OFx1N0RCMlx1OTk5Nlx1OTgwMVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI0YzRlMGI0NDE1XCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJodHRwczpcL1wvd3d3LmJhbmtjaGIuY29tXCI+PFwvZnVuYz4gICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTdEQjJcdTdBRDlcdTVDMEVcdTg5QkRcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwic2l0ZW1hcFwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwic2l0ZW1hcC5qc3BcIj48XC9mdW5jPiAgICA8XC9mdW5jPiAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJhcmVhX2Z1bGxcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiSG9tZVwiIGRlc2NyaXB0aW9uPVwiSG9tZVwiIGlkPVwiaW5kZXhfZW5nXCIgcGFnZT1cImluZGV4X2VuZ1wiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgIDxmdW5jIGxheW91dD1cInN1YmFyZWFfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIk1lc3NhZ2UgZnJvbSB0aGUgQ2hhaXJwZXJzb25cIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiMjZmYzhhYmExNVwiIHBhZ2U9XCIyNmZjOGFiYTE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICA8ZnVuYyBsYXlvdXQ9XCJcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiTWVjaGFuaXNtIG9mIFN1c3RhaW5hYmxlIERldmVsb3BtZW50XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjhhNWU1N2NhMTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIk9yZ2FuaXphdGlvbiBhbmQgTWVjaGFuaXNtIG9mIFN1c3RhaW5hYmxlIERldmVsb3BtZW50XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cImNjMGNkYjUzMTVcIiBwYWdlPVwiY2MwY2RiNTMxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJTdGFrZWhvbGRlciBFbmdhZ2VtZW50IGFuZCBNYXRlcmlhbCBUb3BpY3MgQW5hbHlzaXNcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYjgyOGViNDYxNVwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIk1hdGVyaWFsIFRvcGljcyBBbmFseXNpc1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJlZmRhYjJiMzE1XCIgcGFnZT1cImVmZGFiMmIzMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiVGhlIGltcG9ydGFuY2UgYW5kIGltcGFjdCBvZiBNYXRlcmlhbCBUb3BpY1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCIyNjA3ZThlNjE1XCIgcGFnZT1cIjI2MDdlOGU2MTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiU3VtbWFyeSBvZiBTdGFrZWhvbGRlciBDb21tdW5pY2F0aW9uIENoYW5uZWxzIGFuZCBDb25jZXJuZWQgVG9waWNzXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjVkN2JmYzQyMTVcIiBwYWdlPVwiNWQ3YmZjNDIxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJNYW5hZ2VtZW50IGFuZCBUYXJnZXQgb2YgTWFqb3IgVG9waWNzXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjNkZGRkYjljMTVcIiBwYWdlPVwiM2RkZGRiOWMxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkVTR1wvQ1NSIFJlcG9ydHNcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiZDc3NjJiYzAxNVwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiaHR0cHM6XC9cL3d3dy5iYW5rY2hiLmNvbVwvY3NyXC9tYXNodXBfZW5nLmpzcD9mdW5jSWQ9NmRiODcyNTIxNVwiPjxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlN0YWtlaG9sZGVyIFF1ZXN0aW9ubmFpcmVcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYmJkYTQ5MDExNVwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiaHR0cHM6XC9cL3d3dy5iYW5rY2hiLmNvbVwvZnJvbnRlbmRcL3N0YWtlaG9sZGVyUXVlc3Rpb24uanNwP2xhbmc9ZW5fdXNcIj48XC9mdW5jPiAgICAgPFwvZnVuYz4gICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJTdXN0YWluYWJsZSBSZXNpbGllbmNlXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjJlMzMzZTUzMTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJDb21wYW55IFByb2ZpbGVcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiNTcyODUxODMxNVwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkNvbXBhbnkgUHJvZmlsZVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI3ZmFlOGEzZDE1XCIgcGFnZT1cIjdmYWU4YTNkMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiQnVzaW5lc3MgUGVyZm9ybWFuY2UgYW5kIFRheCBHb3Zlcm5hbmNlXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjQ1ZWUxOGQ5MTVcIiBwYWdlPVwiNDVlZTE4ZDkxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkNvcnBvcmF0ZSBHb3Zlcm5hbmNlXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjhjNDBlODU3MTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJDb3Jwb3JhdGUgR292ZXJuYW5jZSBGcmFtd29yayAmYW1wOyB0aGUgQm9hcmQgb2YgRGlyZWN0b3JzXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjRhNjJjZDZiMTVcIiBwYWdlPVwiNGE2MmNkNmIxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJQZXJmb3JtYW5jZSAmYW1wOyBSZW11bmVyYXRpb24gb2YgQm9hcmQgb2YgRGlyZWN0b3JzXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjI4Yjc5NGFkMTVcIiBwYWdlPVwiMjhiNzk0YWQxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJQYXJ0aWNpcGF0aW5nIGluIFRyYWRlIEFzc29jaWF0aW9ucyBhbmQgTG9iYnlpbmdcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiNmY5MzYzOGQxNVwiIHBhZ2U9XCI2ZjkzNjM4ZDE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgPFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJCdXNpbmVzcyBJbnRlZ3JpdHlcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiMDhmMGZmOWMxNlwiIHBhZ2U9XCIwOGYwZmY5YzE2XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiQ29tcGxpYW5jZVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI5MzAxMWRjMTE1XCIgcGFnZT1cIjkzMDExZGMxMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJBbnRpLU1vbmV5IExhdW5kZXJpbmcgYW5kIENvdW50ZXJpbmcgRmluYW5jaW5nIG9mIFRlcnJvcmlzbVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJjMTg1ODQ5MDE1XCIgcGFnZT1cImMxODU4NDkwMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJSaXNrIE1hbmFnZW1lbnQgYW5kIEF1ZGl0XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cImFlOTg2ZTRjMTVcIiBwYWdlPVwiYWU5ODZlNGMxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiUmlzayBNYW5hZ2VtZW50IGFuZCBBdWRpdFwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCIyNmJiZGFkNDE2XCIgcGFnZT1cIjI2YmJkYWQ0MTZcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiRW1lcmdpbmcgUmlzayBNYW5hZ2VtZW50XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjA2ZDY3M2M2MTZcIiBwYWdlPVwiMDZkNjczYzYxNlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJJbnRlbGxlY3R1YWwgUHJvcGVydHkgTWFuYWdlbWVudFwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI2MDAzMDc2YTE2XCIgcGFnZT1cIjYwMDMwNzZhMTZcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJJbmZvcm1hdGlvbiBTZWN1cml0eSBhbmQgRGF0YSBQcml2YWN5XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjVkYjNjY2NhMTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJJbmZvcm1hdGlvbiBTZWN1cml0eSBNZWNoYW5pc21cIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiOWZmZjc1ZTMxNVwiIHBhZ2U9XCI5ZmZmNzVlMzE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlBlcnNvbmFsIEluZm9ybWF0aW9uIFByb3RlY3Rpb25cIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYjM3OTI0YWQxNVwiIHBhZ2U9XCJiMzc5MjRhZDE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgPFwvZnVuYz4gICAgIDxcL2Z1bmM+ICAgICA8ZnVuYyBsYXlvdXQ9XCJcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiU3VzdGFpbmFibGUgRW52aXJvbm1lbnQgYW5kIEZpbmFuY2VcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiOGNlZWM3ZTQxNVwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+ICAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkNsaW1hdGUtIGFuZCBOYXR1cmUtUmVsYXRlZCBEaXNjbG9zdXJlc1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCIxYzZiYWI3ZjE1XCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiR292ZXJuYW5jZSBhbmQgU3RyYXRlZ3lcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiNTZkMzViY2MxNVwiIHBhZ2U9XCI1NmQzNWJjYzE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiQ2xpbWF0ZSBhbmQgTmF0dXJlIFJpc2sgTWFuYWdlbWVudFwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI0ZWJjNzEwNzE1XCIgcGFnZT1cIjRlYmM3MTA3MTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkdyZWVuaG91c2UgR2FzIFJlZHVjdGlvbiBhbmQgTWFuYWdlbWVudFwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCIzZjY0ZjFiMjE1XCIgcGFnZT1cIjNmNjRmMWIyMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlN1c3RhaW5hYmxlIEVuZXJneSBhbmQgUmVzb3VyY2UgTWFuYWdlbWVudFwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI2Y2U3YjU0ZTE1XCIgcGFnZT1cIjZjZTdiNTRlMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJTdXN0YWluYWJsZSBQcm9jdXJlbWVudCBNYW5hZ2VtZW50XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cImMxNWE0ODI4MTVcIiBwYWdlPVwiYzE1YTQ4MjgxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlJlc3BvbnNpYmxlIEZpbmFuY2VcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYmViNjE5YWQxNVwiIHBhZ2U9XCJiZWI2MTlhZDE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJTdXN0YWluYWJsZSBGaW5hbmNlXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjQ4MzAyYTRlMTVcIiBwYWdlPVwiNDgzMDJhNGUxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJSZXNwb25zaWJsZSBJbnZlc3RtZW50XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjZjODE2YWQzMTZcIiBwYWdlPVwiNmM4MTZhZDMxNlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJSZXNwb25zaWJsZSBGaW5hbmNpbmdcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiZDY4ZmFkNjcxNVwiIHBhZ2U9XCJkNjhmYWQ2NzE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkVxdWF0b3IgUHJpbmNpcGxlc1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI5MzgwOTY0NDE1XCIgcGFnZT1cIjkzODA5NjQ0MTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiQ3VzdG9tZXIgUmlnaHRzIGFuZCBJbnRlcmVzdHNcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiNTRmZjA4ZWUxNVwiIHBhZ2U9XCI1NGZmMDhlZTE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkRpZ2l0YWwgSW5ub3ZhdGlvbiBTZXJ2aWNlc1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI2ZThkYjE0YTE1XCIgcGFnZT1cIjZlOGRiMTRhMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiRmluYW5jaWFsIEluY2x1c2lvblwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCIwZGI2MjRhODE2XCIgcGFnZT1cIjBkYjYyNGE4MTZcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiR3JlZW4gVHJhbnNpdGlvblwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI5ODRmYjAxMjE1XCIgcGFnZT1cIjk4NGZiMDEyMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8XC9mdW5jPiAgICAgPFwvZnVuYz4gICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJIYXBweSBXb3JrcGxhY2UgYW5kIFNvY2lhbCBJbmNsdXNpb25cIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiY2M4Zjg3ZmUxNVwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiSHVtYW4gUmlnaHRzIFByb3RlY3Rpb25cIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiODA5ZjVhMzExNVwiIHBhZ2U9XCI4MDlmNWEzMTE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiRGl2ZXJzaXR5IGFuZCBFcXVhbGl0eVwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI0OGRlMjZhMTE1XCIgcGFnZT1cIjQ4ZGUyNmExMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJTZXh1YWwgSGFyYXNzbWVudCBQcmV2ZW50aW9uXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjRhNzJhZjhiMTVcIiBwYWdlPVwiNGE3MmFmOGIxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJUYWxlbnQgQXR0cmFjdGlvbiBhbmQgUmV0ZW50aW9uXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjhlNzIwOWVkMTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJFbXBsb3llZSBDb21wb3NpdGlvbiBhbmQgVGFsZW50IEF0dHJhY3Rpb25cIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiY2EyNjQxZjMxNVwiIHBhZ2U9XCJjYTI2NDFmMzE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiRW1wbG95ZWUgQ29tcGVuc2F0aW9uIGFuZCBCZW5lZml0c1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJkMTZlZTBkNzE1XCIgcGFnZT1cImQxNmVlMGQ3MTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiRW1wbG95ZWUgQ29tbXVuaWNhdGlvbiBDaGFubmVsXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjYwNWJmZWRmMTVcIiBwYWdlPVwiNjA1YmZlZGYxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiRW1wbG95ZWUgQ3VsdGl2YXRpb24gYW5kIERldmVsb3BtZW50XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjRlNDAyZmJlMTVcIiBwYWdlPVwiNGU0MDJmYmUxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIk9jY3VwYXRpb25hbCBTYWZldHkgYW5kIEhlYWx0aFwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI5MWFhMWM0MTE1XCIgcGFnZT1cIjkxYWExYzQxMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJDaGFyaXRhYmxlIFN0cmF0ZWd5IGFuZCBJbmZsdWVuY2VcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYzYzNGE5MzIxNVwiIHBhZ2U9XCJjNjM0YTkzMjE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudF9lbmdcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiRmluYW5jaWFsIExpdGVyYWN5IEVkdWNhdGlvblwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJkMzMxYWNiNTE1XCIgcGFnZT1cImQzMzFhY2I1MTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgIDxcL2Z1bmM+ICAgICA8ZnVuYyBsYXlvdXQ9XCJcIiBpc19vcGVuPVwiWVwiIHVsY2xhc3M9XCJcIiBuYW1lPVwiQXdhcmRzIGFuZCBSZWNvZ25pdGlvblwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJhNjdmMzQ0YzE1XCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJIb25vcnMsIFJlY29nbml0aW9ucyBhbmQgU3VzdGFpbmFibGUgUGVyZm9ybWFuY2VzXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjEzYWUxNzk2MTVcIiBwYWdlPVwiMTNhZTE3OTYxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkludGVybmF0aW9uYWwgQ2VydGlmaWNhdGlvbnNcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiNjE2YzFlNjExNVwiIHBhZ2U9XCI2MTZjMWU2MTE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgICA8XC9mdW5jPiAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkZyaWVuZGx5IExpbmtzXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjM4ZmQ5ZDdjMTVcIiBwYWdlPVwiXCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPiAgICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkZyaWVuZGx5IExpbmtzXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjJjYjA0NzY1MTVcIiBwYWdlPVwiMmNiMDQ3NjUxNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgPFwvZnVuYz4gICAgPFwvZnVuYz4gICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlN1YiBtZW51XCIgZGVzY3JpcHRpb249XCJTdWIgbWVudVwiIGlkPVwidG9wbWVudTFfZW5nXCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj4gICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJTaXRlbWFwXCIgZGVzY3JpcHRpb249XCJcIiBpZD1cInNpdGVtYXBfZW5nXCIgcGFnZT1cIlwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJzaXRlbWFwX2VuZy5qc3BcIj48XC9mdW5jPiAgICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIkNISU5FU0VcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiYTFhNDE0MjMxNVwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiaW5kZXguanNwXCI+PFwvZnVuYz4gICAgPFwvZnVuYz4gICAgPGZ1bmMgbGF5b3V0PVwiXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NTE3Nlx1NEVENlwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJvdGhlclwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+ICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50XCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlx1NEUwQlx1OEYwOVx1NkMzOFx1N0U4Q1wvXHU0RjAxXHU2OTZEXHU3OTNFXHU2NzAzXHU4Q0FDXHU0RUZCXHU1ODMxXHU1NDRBXHU2NkY4XCIgZGVzY3JpcHRpb249XCJcIiBpZD1cIjY2YzRjNTExMTVcIiBwYWdlPVwiNjZjNGM1MTExNVwiIGxpY2xhc3M9XCJcIiBpY29uY2xhc3M9XCJcIiB1cmw9XCJcIj48XC9mdW5jPiAgICAgPGZ1bmMgbGF5b3V0PVwic3ViY29udGVudFwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJcdTY2MEVcdTU0RjJcdTZFMkNcdThBNjZcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiZGVjMTgyYjcxNVwiIHBhZ2U9XCJkZWMxODJiNzE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgIDxcL2Z1bmM+ICAgIDxmdW5jIGxheW91dD1cIlwiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJPdGhlclwiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCJvdGhlcl9lblwiIHBhZ2U9XCJcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+ICAgICA8ZnVuYyBsYXlvdXQ9XCJzdWJjb250ZW50X2VuZ1wiIGlzX29wZW49XCJZXCIgdWxjbGFzcz1cIlwiIG5hbWU9XCJEb3dubG9hZCBFU0cgUmVwb3J0c1wiIGRlc2NyaXB0aW9uPVwiXCIgaWQ9XCI2ZGI4NzI1MjE1XCIgcGFnZT1cIjZkYjg3MjUyMTVcIiBsaWNsYXNzPVwiXCIgaWNvbmNsYXNzPVwiXCIgdXJsPVwiXCI+PFwvZnVuYz4gICAgIDxmdW5jIGxheW91dD1cInN1YmNvbnRlbnRfZW5nXCIgaXNfb3Blbj1cIllcIiB1bGNsYXNzPVwiXCIgbmFtZT1cIlRlc3RcIiBkZXNjcmlwdGlvbj1cIlwiIGlkPVwiNDE1NzEyYTkxNVwiIHBhZ2U9XCI0MTU3MTJhOTE1XCIgbGljbGFzcz1cIlwiIGljb25jbGFzcz1cIlwiIHVybD1cIlwiPjxcL2Z1bmM+ICAgIDxcL2Z1bmM+ICAgPFwvZnVuY3M+ICA8XC9nYXJkZW4+IDxcL2JvZHk+PFwvaHRtbD4=
Jump to main content
.png)
For the best experience, change the screen to portrait mode.
|
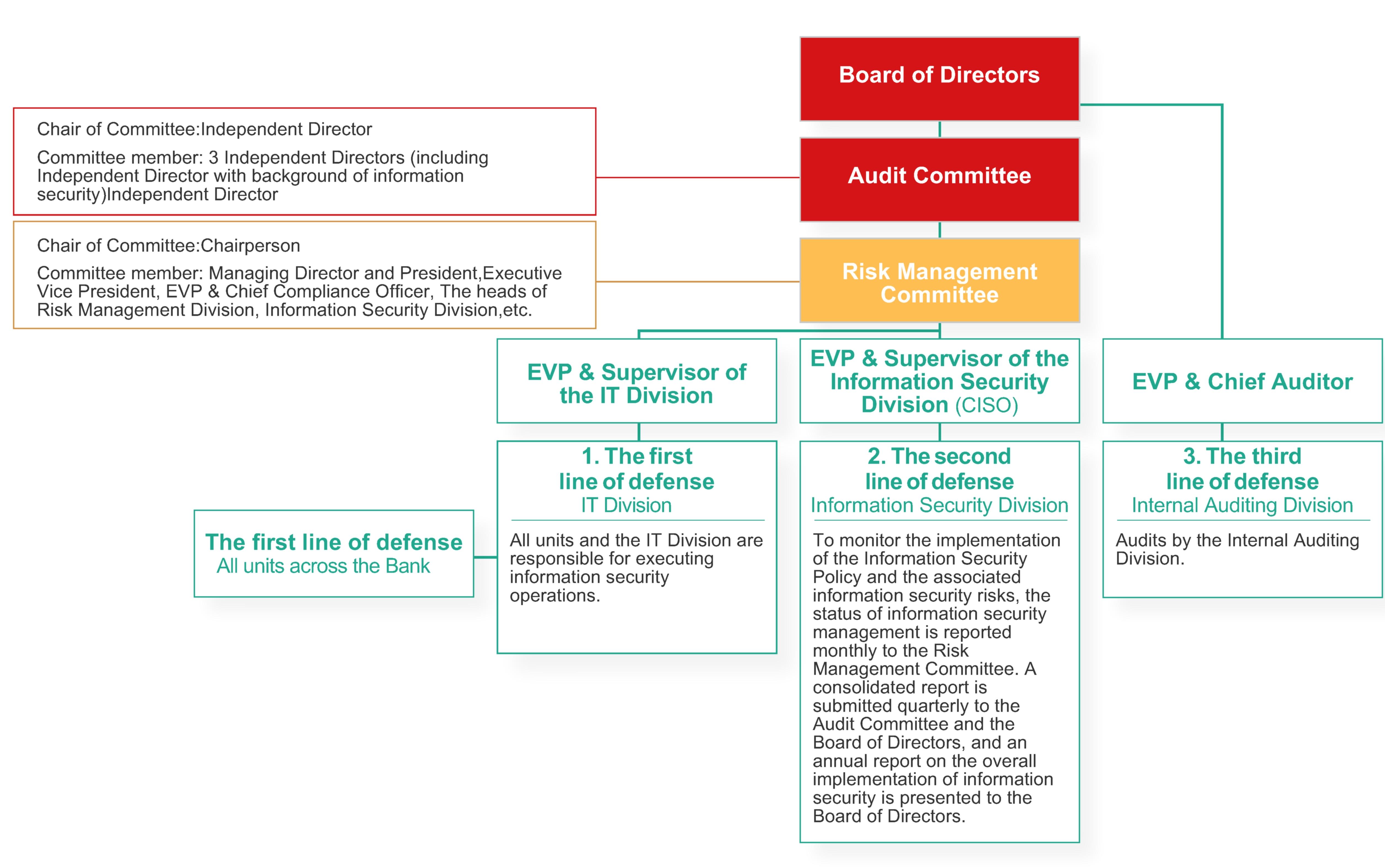
Course
|
Target personnel
|
Total training hours
|
|
Information security awareness training in Chinese and English
|
All employees (including those in overseas branches and excluding general workers and drivers)
|
19,575 hours
|
|
Information security awareness education and training for highrisk personnel
|
Information and security personnel
|
314 hours
|
|
Business Continuity Management (BCM) Awareness Training
|
157 hours
|
|
|
Courses related to information security
|
Information security specialists
|
591hours
|
|
SWIFT Education and Training
|
SWIFT authorized personnel
|
82 hours
|